Docker networking refers to the set of technologies and functionalities within Docker that enable communication between containers, between containers and the host machine, and between containers and external networks. It allows containers to interact with each other and with external systems securely and efficiently.
Container networking refers to the ability for containers to connect to and communicate with each other, or to non-Docker workloads.
Containers have networking enabled by default, and they can make outgoing connections. A container has no information about what kind of network it’s attached to, or whether their peers are also Docker workloads or not. A container only sees a network interface with an IP address, a gateway, a routing table, DNS services, and other networking details. That is, unless the container uses the none network driver.
👉 Here are the key points to understand about Docker networking:
Container Communication: Docker networking enables containers running on the same host to communicate with each other using IP addresses or DNS names. This communication can be established within a single Docker host or across multiple Docker hosts in a cluster.
Network Isolation: Docker networking provides network isolation between containers, ensuring that each container has its own network stack and IP address.
Default Bridge Network: When you install Docker, it automatically creates a default bridge network called
bridge. Containers connected to this network can communicate with each other using container names as DNS names. The default bridge network is suitable for most development and testing scenarios.Custom Networks: Docker allows users to create custom networks using the
docker network createcommand. This feature enables better control over networking configurations such as IP address ranges, subnets, and DNS settings.Networking Drivers: Docker supports different networking drivers such as bridge, host, overlay, macvlan, and none. Each driver has specific use cases and functionalities, providing flexibility in how containers interact with networks.
Container-to-Container Communication: Containers within the same network can communicate with each other using their container names as hostnames. Docker’s built-in DNS server resolves container names to their respective IP addresses within the network.
Container-to-External Network Communication: Docker containers can communicate with external networks and services through port mappings or by connecting containers to external networks using custom bridge networks or host networking mode.
Service Discovery and Load Balancing: Docker networking integrates with service discovery and load balancing mechanisms, such as Docker Swarm’s built-in DNS-based service discovery and load balancing features. This allows containers to discover and communicate with services running on different containers or nodes in a cluster.
Network Security: Docker networking provides security features such as network segmentation, firewall rules, and network policies to control inbound and outbound traffic, ensuring secure communication between containers and networks.
Scalability and Orchestration: Docker networking is scalable and integrates seamlessly with container orchestration platforms like Docker Swarm and Kubernetes, allowing for dynamic network configurations and efficient management of containerized applications.
👉 Types of networking in Docker
Bridge Network:
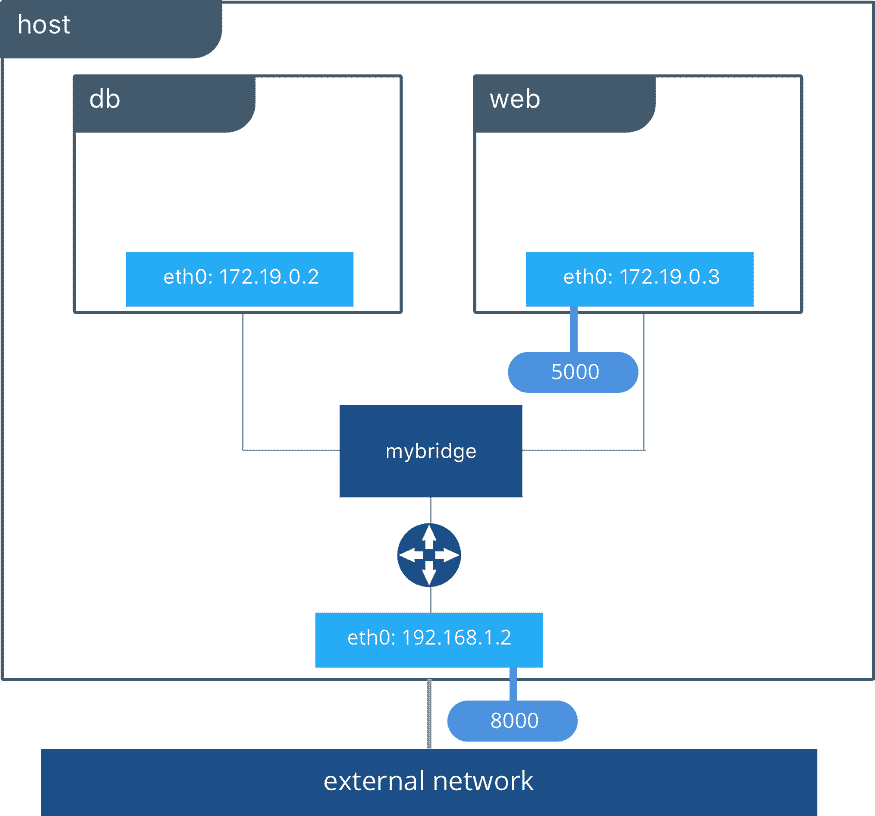
Bridge network is a default network created automatically when you deploy a container. Bridge network uses a software bridge that allows containers connected to the same bridge network to communicate. Bridge networks used on containers that are running on the same Docker daemon host. The bridge network creates a private internal isolated network to the host so containers on this network can communicate.
The Bridge Network in Docker is a default networking mode that enables communication between containers on the same Docker host. It provides network isolation, giving each container its own IP address and DNS configuration. Containers connected to the bridge network can communicate using their IP addresses or container names, facilitated by Docker’s built-in DNS server. Additionally, bridge networking allows containers to access the internet through NAT rules. It’s commonly used in development and testing environments for local container communication. However, for more complex networking needs or distributed systems across multiple hosts, other Docker networking modes may be preferred.
Host Network:
The Host Network mode in Docker allows containers to share the host’s networking stack directly, bypassing Docker’s network isolation. In this mode, containers use the host’s IP address, network interfaces, and routing table, resulting in improved networking performance. Containers on the host network can access external networks and services without the overhead of network address translation (NAT) or port mapping. However, this mode lacks network isolation between containers and may not be suitable for scenarios requiring strict network segmentation. Host networking is commonly used for applications requiring maximum network performance or direct access to host networking interfaces, such as network-intensive services or legacy applications.

Overlay Network:
Overlay networking is used if container on node A wants to talk to node B then to make communication between them we use Overlay networking. Overlay networking uses VXLAN to create an Overlay network. This has the advantage of providing maximum portability across various cloud and on-premises networks. By default, the Overlay network is encrypted with the AES algorithm.
Overlay networking in Docker, especially in Docker Swarm, is used to facilitate communication between containers across different Docker hosts or nodes within a Swarm cluster. When a container on one node (let’s say node A) needs to communicate with a container on another node (node B), overlay networking comes into play.
Overlay networking leverages technologies like VXLAN (Virtual Extensible LAN) to create a virtual network overlay that spans all nodes in the Swarm cluster. This overlay network enables seamless communication between containers regardless of their physical host, providing a unified network environment for distributed applications.
One of the key advantages of overlay networking is its portability across various cloud environments and on-premises networks. Containers can communicate across different infrastructure setups without needing to worry about underlying network configurations, thanks to the abstraction provided by overlay networking.
Macvlan Network:
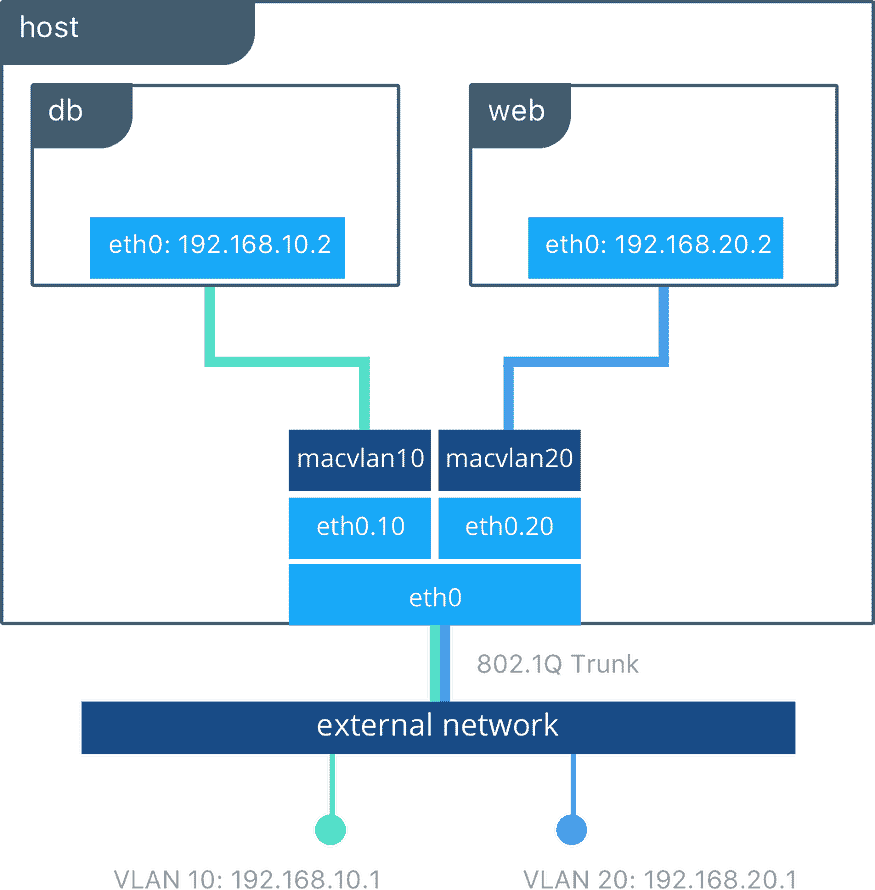
Macvlan network is used to connect applications directly to the physical network. By using the macvlan network driver to assign a MAC address to each container, also allow having full TCP/Ip stack. Then, the Docker daemon routes traffic to containers by their MAC addresses. You can isolate your macvlan networks using different physical network interfaces. This is used in legacy applications which require MAC address.
Macvlan networking in Docker is a mode that gives each container its own MAC address, making them appear as separate physical devices on the network. This enables containers to directly communicate with external networks without going through the Docker host’s network stack. Macvlan networking is beneficial for scenarios where containers require direct access to the underlying network infrastructure, such as when running network-intensive applications or services that need to expose specific ports. It provides improved network performance, isolation, and flexibility compared to bridge networking, making it suitable for applications needing container-to-network communication without network address translation (NAT) overhead.
ipvlan:
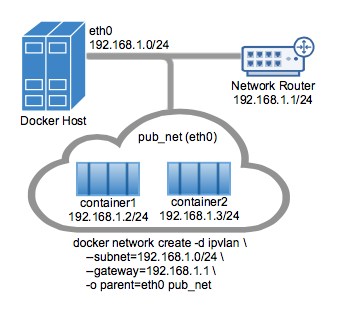
IPvlan networks give users total control over both IPv4 and IPv6 addressing. The VLAN driver builds on top of that in giving operators complete control of layer 2 VLAN tagging and even IPvlan L3 routing for users interested in underlay network integration.
