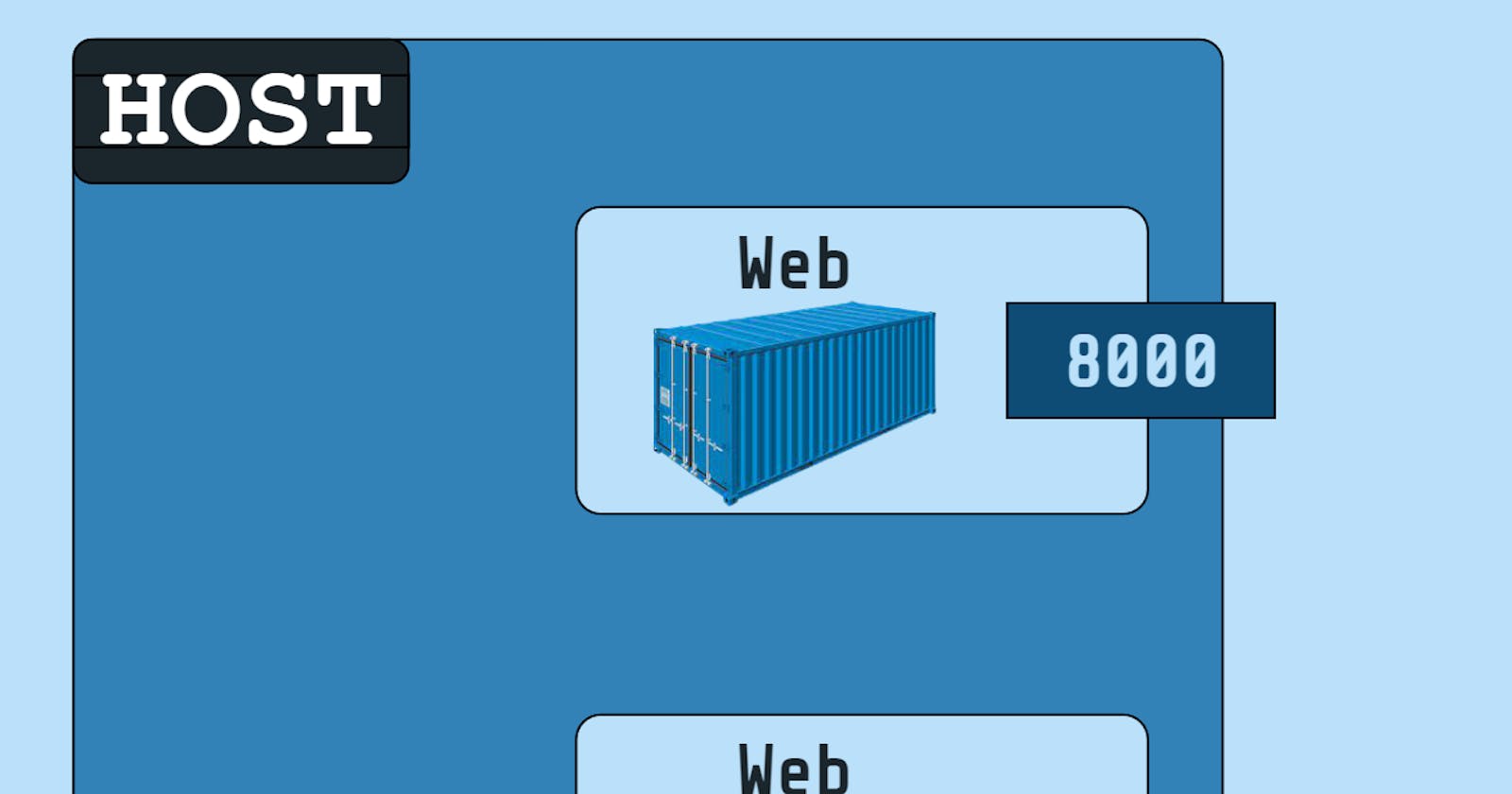
The Host network driver in Docker is a networking mode that allows containers to directly use the networking stack of the Docker host machine. When a container is run with the Host network driver, it bypasses Docker’s network abstraction layer and gains direct access to the host’s network interfaces, routing table, and ports. This means that the container shares the same network namespace as the host, using the host’s IP address and network configuration.
If you use the host network mode for a container, that container's network stack isn't isolated from the Docker host (the container shares the host's networking namespace), and the container doesn't get its own IP-address allocated. For instance, if you run a container which binds to port 80 and you use host networking, the container's application is available on port 80 on the host's IP address.
👉Use cases:
Host mode networking in Docker can be beneficial for several use cases where direct access to the host’s networking stack is required. Here are some scenarios where host mode networking can be useful:
High-Performance Applications: Host mode networking is ideal for applications that demand maximum network performance and low latency. By bypassing Docker’s networking abstraction layer, containers can achieve better throughput and reduced overhead, making it suitable for high-performance workloads such as databases or real-time streaming services.
Networking Tools and Utilities: Networking tools or utilities that require direct access to network interfaces or network configuration on the host machine can benefit from host mode networking. This includes tools like network monitoring agents, packet sniffers, or VPN clients that need full access to the host’s network stack.
Legacy Applications: Legacy applications that are designed to run directly on the host and expect to bind to specific host ports can be containerized using host mode networking. This allows the containerized application to behave similarly to how it would run natively on the host without network address translation (NAT) or port mapping.
Single-Container Deployment: In cases where a single container needs to expose multiple services on different ports without conflicts, host mode networking can simplify the configuration. Each service within the container can bind directly to the corresponding port on the host, avoiding port collision issues.
Network Troubleshooting and Debugging: During network troubleshooting or debugging tasks, using host mode networking can provide a clear view of network traffic and behavior by directly accessing host interfaces and routing tables. This can be useful for diagnosing network-related issues within containers.
Containerized Network Services: Certain network services or daemons running inside containers may require access to low-level network functionalities that are only available in the host’s networking stack. Host mode networking allows these services to operate with full network capabilities.
Integration with Host Services: Applications that need seamless integration with host services or rely on specific network configurations present on the host machine can benefit from host mode networking. This ensures compatibility and consistent behavior between containerized services and host-level networking setups.
👉Limitations of the host driver
Lack of Network Isolation: Containers using the Host network driver share the same networking namespace as the host machine, leading to reduced network isolation. This means that processes running inside the container have full access to the host’s network interfaces, potentially increasing security risks if not properly configured.
Port Binding Conflicts: Since containers using the Host network driver share the same network stack as the host, conflicts can occur if multiple containers attempt to bind to the same ports on the host. This can lead to port binding errors and service disruption.
Security Concerns: Host mode networking reduces network isolation between containers and the host, which can pose security risks, especially in multi-tenant environments. Containers running in Host mode have direct access to host network interfaces and services, potentially exposing sensitive information or resources.
Limited Scalability: Host mode networking may not scale well in environments with a large number of containers or distributed systems. It may not be suitable for complex networking architectures or deployments requiring advanced network routing and segmentation.
Only works on Linux machines: The Host network driver in Docker only works on Linux machines. This limitation arises due to the way the Host networking mode is implemented and how it leverages the underlying networking capabilities of the Linux kernel.
👉Example using host driver:
To use the Host network driver in Docker, you can specify the --network=host option when running a container. This option tells Docker to use the host's networking stack directly for the container, allowing the container to share the same network namespace as the host machine. Here's how you can use the Host network driver:
For example, To run an Nginx container named “app2” using the Host network driver in Docker:
docker run -d --network=host --name app2 nginx
Let’s break down the command:
docker run: This is the command to run a new Docker container.-d: This flag runs the container in detached mode, meaning it runs in the background.--network=host: This option specifies that the container should use the host's networking stack directly, using the Host network driver.--name app2: This option gives the container the name "app2" so that you can refer to it easily.nginx: This is the name of the Docker image to use for the container. In this case, we're using the Nginx official image.
After running this command, Docker will start a new Nginx container named “app2” using the Host network driver.
Use the docker inspect command to view detailed information about the container, including its network settings:
docker inspect app2
Here’s an example of what the output might look like for a container named “app2” running with the Host network driver:
[
{
"Id": "container_id",
"Created": "2024-03-25T12:34:56.000Z",
"State": {
...
},
"NetworkSettings": {
"Networks": {
"host": {
"IPAMConfig": null,
"Links": null,
"Aliases": null,
"NetworkID": "",
"EndpointID": "",
"Gateway": "",
"IPAddress": "",
"IPPrefixLen": 0,
"IPv6Gateway": "",
"GlobalIPv6Address": "",
"GlobalIPv6PrefixLen": 0,
"MacAddress": "",
"DriverOpts": null
}
},
...
},
...
}
]
To check the logs of the “app2” container, you would use:
docker logs app2
To clean up and remove the Docker containers that were created during the hands-on lab, you can use the docker rm command.
docker rm -f app2
This command removes the containers named “app2”. The -f flag is used to force the removal of the containers even if they are currently running.