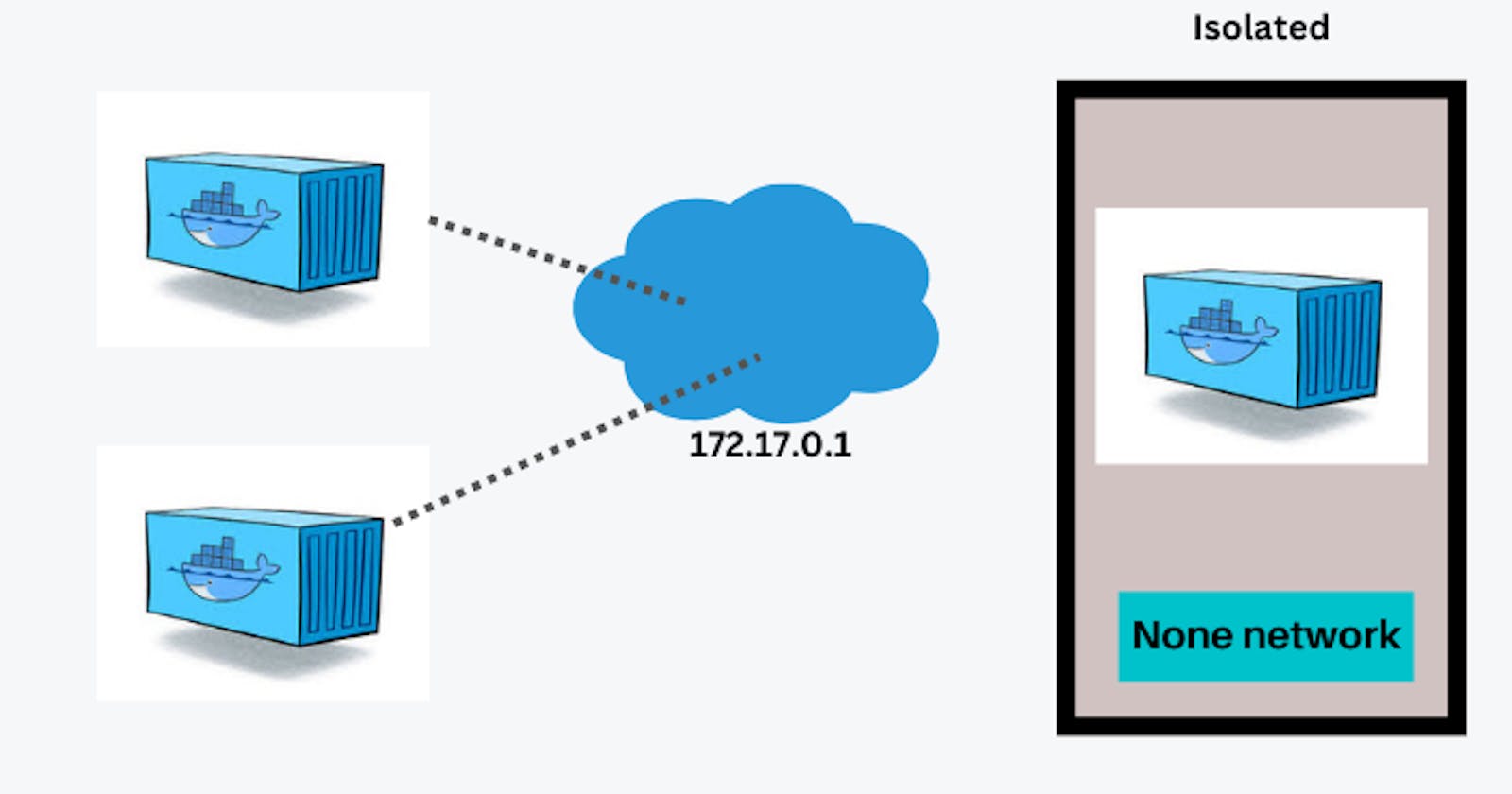
The “none” network driver in Docker is a special type of network that provides complete isolation for a container from any external network. When you attach a container to the “none” network, it means the container has no network connectivity whatsoever. This can be useful in certain scenarios where you want to prevent a container from communicating with other containers or external networks.
If you want to completely isolate the networking stack of a container, you can use the --network none flag when starting the container. Within the container, only the loopback device is created.
👉 Possible Use Cases:
The “none” network driver in Docker provides complete network isolation for containers, making it suitable for specific use cases where network connectivity is not required or should be restricted. Here are some possible scenarios where you might consider using the “none” network driver:
Highly Sensitive Applications: For applications handling highly sensitive data or running critical processes, isolating them from any network connectivity using the “none” network driver adds an extra layer of security.
Isolation from Malware or Attacks: In environments where there’s a higher risk of network-based attacks or malware, running containers on the “none” network can reduce the attack surface.
Network Debugging: When debugging networking issues within a container or testing network-related functionalities, isolating the container using the “none” network driver helps eliminate external network interference.
Simulating Network Outages: For testing how applications behave during network outages or when connectivity is lost, using the “none” network driver allows you to simulate these scenarios effectively.
Stand-Alone Containers: Containers that do not require any external dependencies or network services can be run on the “none” network to ensure they operate independently.
Resource Isolation: Isolating containers with resource-intensive tasks or specific workloads from the network can prevent network-related performance impacts.
Transient Containers: Containers that are spun up temporarily for specific tasks or short-lived processes can be attached to the “none” network to minimize exposure and clean up automatically after use (
--rmflag).
👉 Example:
Here’s an example of running the ip link show command inside an Alpine container that is attached to the "none" network driver:
First, start an Alpine container named app1 with the "none" network driver:
docker run -it --name app1 --network=none alpine sh
Inside the container’s shell (sh), run the ip link show command to display network interfaces:
ip link show
The output of ip link show in an Alpine container attached to the "none" network driver will typically look like this:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: eth0@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT group default
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
Explanation of the output:
lo: Loopback interface, which is always present.eth0@if2: Virtual Ethernet interface (eth0) with MAC address02:42:ac:11:00:02and link-netnsid 0. This is typically assigned by Docker when using the "none" network driver.